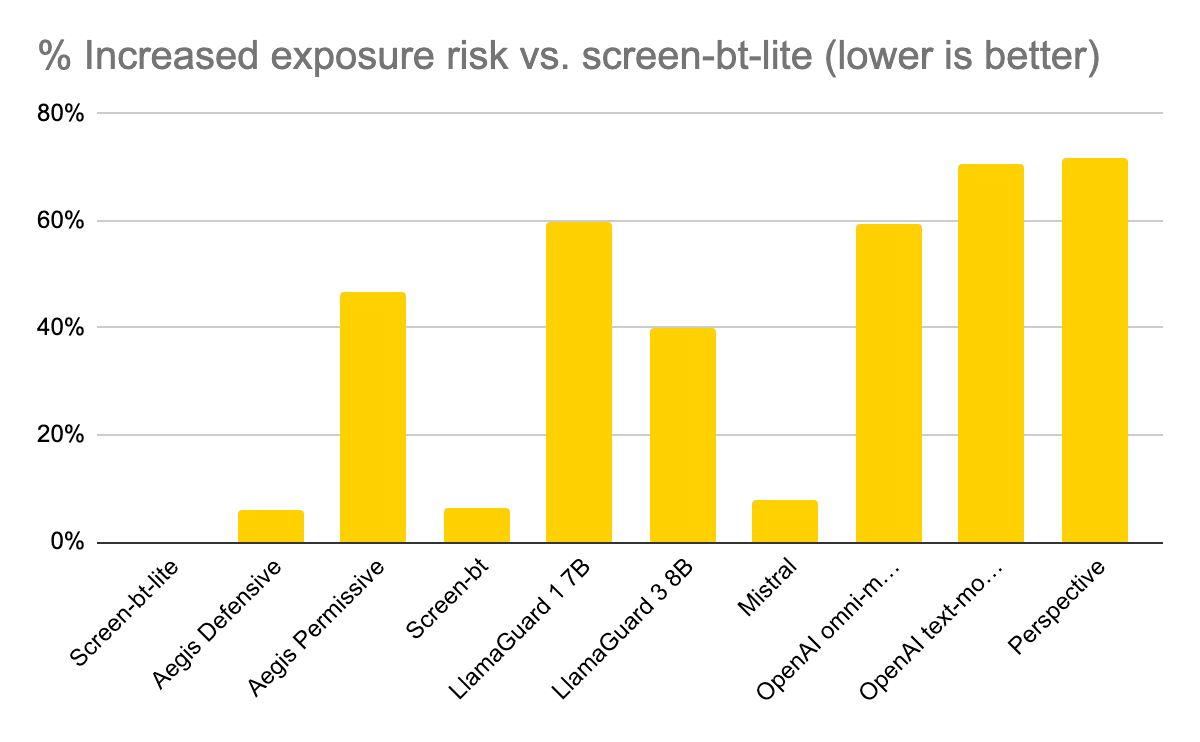
Cloud data breaches pose an ever-increasing concern for many businesses, particularly those integrating AI and large language models (LLMs) into their products. According to Forbes, today’s cloud security experts express particular concerns about cloud misconfigurations, unauthorized access, distributed denial-of-service (DDoS) attacks, data privacy and safety, and unsecured application programming interfaces (APIs). Business leaders are on the hunt for cloud data protection best practices to address these potential threats.
Using the six best practices listed below, organizations can mitigate risks and implement a robust cloud data security strategy that can unlock data for safe use in AI and LLM applications.
Six cloud data protection best practices
To address the biggest security concerns haunting the modern cloud market, organizations need the latest cloud data protection best practices. When combined, these six techniques can boost cloud security significantly while maintaining – and even improving – the performance of genAI and LLM models.
| Cloud Data Protection Best Practices | |
|---|---|
| Best Practice | Result |
| Policy-based access controls (PBACs) | Controls access based on a user’s responsibilities and business security policies. This adaptable strategy allows businesses to change access privileges in response to expanding business values or needs. |
| Identity and access management (IAM) coupled with data security | Ensures each person in the organization has access to the tools and data they need to complete tasks related to their positions. This requires organizations to verify identity and limit data access by role. It’s best implemented with a strong zero-trust data security policy. |
| Sensitive data discovery, removal, masking, replacement | Discovers Personally Identifiable Information (PII) and other sensitive data stored in cloud data lakes or used in LLM prompts and responses at inference time. This process also includes removing this data when possible. It’s important to mask essential data in-transit or use synthetic data as a replacement. |
| Centralized data security platforms | Uses a fully integrated cloud data security platform to manage security policies, compliance, and data governance across all cloud services. |
| Automated provisioning and configuration management | Provisioning (the process of setting up IT infrastructure) is a time-consuming process when performed manually. It’s also prone to human error. The same is true for configuration management (the process of maintaining system configurations according to desired settings). As organizations scale, provisioning and configuration become harder to manage manually and can create security vulnerabilities due to misconfigurations. Automation makes these processes more secure and efficient. |
| Security behavior and culture programs (SBCPs) | Promotes a company-wide culture of strong security and ensures all stakeholders take part in scheduled training, understand their security responsibilities, and hold each other accountable for keeping cloud data secure. |
How to implement these cloud data protection best practices
Policy-based access controls:
- Assign each access request with the following attributes.
- Subject (job title or department).
- Object (a description of the accessible resource).
- Action (the action a Subject is attempting, such as a read-only privilege).
- Context (the time, location, and circumstances of the access attempt).
- Track this information using a cloud data visualization tool.
- Set up automated alerts for access anomalies.
- Reassign attributes as business goals or security needs change.
Identity and access management (IAM) coupled with data security:
- Introduce a zero-trust data security protocol, which requires every user to be authenticated and authorized before accessing data.
- Implement least-privilege policies, which only give authenticated users access to data necessary to complete specific tasks.
Sensitive data discovery, removal, masking, replacement:
- Identify PII and other sensitive data based on the latest compliance standards and internal business parameters. Automate this process when possible to ensure sensitive data isn’t miscategorized and that all data entering cloud data lakes is protected immediately. Ensure tools have high discovery accuracy to mitigate false negatives and positives.
- Remove PII and other sensitive data that isn’t critical to operations (this is especially important for GDPR compliance).
- Mask sensitive data in both training data sets and real-time inferencing data sets using automated masking algorithms. Replace sensitive data with synthetic data to both protect real data from leaks and improve genAI and LLM functionality.
Centralized data security platforms:
- Look for data security platforms that provide:
- Security policy management, including authorization and authentication.
- Compliance, including consent management for regulations like the GDPR or HIPAA.
- Data governance, including a full accounting of all data stored, who has access to this data, when access occurs, and what, if anything, changed after the user gained access.
Automated provisioning and configuration management:
- Using an automated provisioning tool, create rules that automatically grant users access rights based on security protocols and policies, as well as their roles.
- Using an automated configuration tool, migrate data safely from on-premises storage to cloud data lakes. Use the same tool to configure systems across regions or cloud platforms.
Security behavior and culture programs (SBCPs):
- Schedule security training at regular intervals and encourage all stakeholders to attend.
- Use FinOps principles to foster a culture of shared responsibility.
- Ensure all teams understand their roles in cloud security and follow these cloud data protection best practices.
One of the simplest ways to implement cloud data protection best practices is by using a strong data privacy platform.
Granica protects sensitive data in the cloud
Granica Screen is a data privacy service that discovers, masks, and generates synthetic data for use in genAI and LLM-based products. Following the latest cloud data protection best practices, Screen scans cloud data lake training files to identify and protect sensitive data automatically, unlocking more data for model training to improve accuracy. With real-time inference protection, Screen enables organizations to safely use LLM-powered applications, leading to better business outcomes. Moreover, Granica Screen deploys entirely within an organization’s cloud environment, ensuring that sensitive data never leaves the secure cloud environment.
Explore an interactive demo of Granica Screen to harness cloud data protection best practices and unlock more data for use in genAI models.