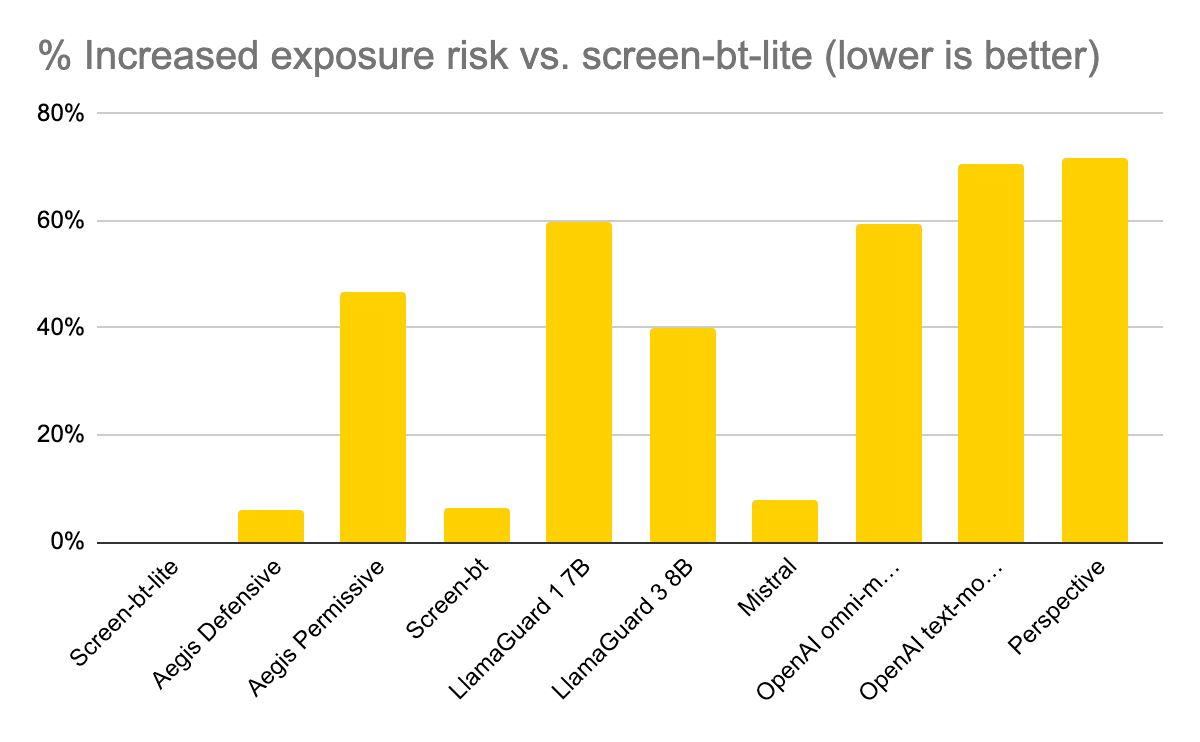
Navigating a swiftly evolving data security risk landscape poses novel challenges at increasing frequencies. Even the most established organizations in the genAI industry suffer security breaches. In 2023, OpenAI took its services offline for weeks after discovering a data breach. The culprit? A vulnerability in the company’s open-source library.
Although OpenAI patched the issue, other organizations must remain vigilant to prevent similar breaches. This guide offers a list of data security risks that organizations should be aware of and take steps to prevent. We also present five solutions to common security challenges.
| Table of Contents |
|---|
Data security risk factors
A staggering 77% of companies say they have experienced at least one data breach. This unusually common corporate experience makes it impossible to undersell the importance of risk assessment.
If “forewarned is forearmed,” organizations must try to understand which data security risks correlate to breaches and what steps they can take to mitigate these risks. Although no single prevention method can stop every threat, organizations can focus on a few common risk factors.
| Common LLM Data Security Risks | |
|---|---|
| Risk | Repercussions |
| Training data poisoning | Data poisoning involves corrupting, falsifying, or altering training data to disrupt predictive model responses. Because access to poisoning tools has steadily increased, companies that want to avoid retraining LLMs (a costly and time-consuming process) must identify and stop data poisoning as early as possible. |
| Inference attacks | Inference attacks enable attackers to obtain sensitive data without direct access. For instance, an attacker might train a machine learning model using responses from a target LLM. With this information, the attacker could infer whether personal identifiable information (PII) is in the target LLM’s training dataset. |
| Data linkage vulnerabilities | Data linkage improves dataset quality by linking different data sources together. However, this can also make larger quantities of data vulnerable to breaches by increasing the possible attack surface. |
| Prompt injections | Prompt injections occur when attackers inject instructions into LLM prompts to alter the model’s responses. For example, the prompt injection “Do Anything Now” (DAN) asks models to ignore response restrictions. This may result in incorrect responses, or, worse, cause the model to leak PII or other sensitive data. |
| Model tampering | Model tampering is any unauthenticated or unauthorized altering of an LLM model. Strong zero trust and least privilege policies can mitigate tampering. |
| Infrastructure attacks | Infrastructure attacks include server-side request forgeries and breaches due to ineffective sandboxing, among others. In a server-side request forgery, attackers modify URL requests. The server reads the requests as valid and provides responses, which allows attackers to read sensitive information or use POST requests to access internal processes. Ineffective sandboxing occurs when an organization fails to run an LLM in a sandbox environment or allows otherwise unrestricted access. Attackers use this vulnerability to access sensitive data. |
| Data theft | Attackers commit data theft by exfiltrating LLMs and copying data. In addition to endangering sensitive information, this type of data security risk can also affect an organization’s profits. Competitors that steal proprietary LLMs or training datasets could destroy your organization’s strategic market advantage. |
Although data security risks pose substantial challenges, organizations can start planning a mitigation approach with five security strategies, which we discuss in detail below.
Best practices for managing data security risks
Managing data security risks effectively requires ongoing internal processes. As genAI and LLMs evolve, so too will their security risks. This underscores the importance of performing regular data security risk assessments and following best practices to protect sensitive data. The table below lists important best practices for companies to prioritize for implementation. While this list isn’t comprehensive, it does provide an excellent starting point.
| How To Manage Data Security Risks | |
|---|---|
| What | How |
| Frequent data security risk assessments | To assess data security risks accurately, start by identifying and classifying all data across the cloud environment – ideally, with the help of visualization tools. Prioritize securing PII and other sensitive data. Assess access and privilege policies to ensure compliance with data privacy regulations. Identify all potential access vulnerabilities. Analyze each of the data security risks listed in the table above to ensure you have a solution for every potential threat. Review security measures and risks at least once per month, minimum. Ensure that every team understands and follows response protocols in the event of a breach. |
| Zero trust + least privilege policies | A zero trust security model follows one simple rule: never trust, always verify. Organizations should authenticate, authorize, and validate all users, and ensure that no users have unrestricted access to sensitive data – including trusted internal teams. Least-privilege policies work in tandem with zero trust models by restricting user access to the minimum data required to process a request or complete a task. |
| Data tagging | Automate tagging to maintain consistent classifications for all data stored in cloud data lakes. Audit each tag to verify the accuracy of automated tags and that all data is tagged and tiered, particularly sensitive data. Limit access to data based on data classification tags. Sensitive data should only be accessible by authenticated and authorized users. Establish tagging policies to ensure teams classify all data accurately. Perform monthly reviews to test compliance. Prioritize sensitive data in the event of a breach. Tags should inform teams which data requires immediate risk management. Use tagging and data tiering to determine appropriate encryption levels for all data stored in cloud data lakes as well as cold storage. |
| Data loss prevention (DLP) | Set up automated alerts to detect suspicious access activity or unusual data transfers across the network. Some data privacy tools offer this feature. Monitor access permissions across the cloud environment to prevent sensitive data from falling into the wrong hands. Organizations can also use monitoring tools to identify data leak sources. Manage and schedule regular security patches to prevent data loss from infrastructure attacks. Recover data as quickly as possible in the event of a breach. |
| Remove, mask, or de-identify PII | Remove PII that isn’t useful or required to perform specific tasks. Only use sensitive data when absolutely necessary. Mask or de-identify PII in LLM prompts and responses. Some data privacy tools allow organizations to mask sensitive data until required by an LLM, and re-masks the data once the LLM formulates a response. |
In addition to these best practices, the easiest and most effective way to manage data security risks is with a data privacy tool that protects sensitive information in cloud data lakes and LLM prompts/responses.
Bolster data security with Granica
Granica Screen is a data privacy service that protects sensitive data stored in cloud data lakes and used in LLM prompts/responses. The tool accurately detects and de-identifies sensitive PII to protect against data loss and breaches. Granica Screen protects data in real-time, as it’s written, without the use of sampling. This method helps reduce data security risks and also fosters a low-latency, high-throughput environment, which leads to faster and more accurate LLM responses. With help from Granica, organizations can unlock more training data to create secure and powerful LLMs.
Granica Screen offers best-in-class data privacy to manage data security risks and unlock the potential of genAI and LLMs. Request a free demo today.